Description
We are hosting a gallery website for public arts, we faced slowness issues however our deployment team decided to utilize HTTP/2 as when scrolling a webpage with multiple images, a web browser can cancel images that fall outside the viewport, meaning that images entering it can load faster. Everything went smoothly in our testing environment but after going live with the new protocol suddenly everything stopped working. We were able to capture the traffic from the web server, can you help us to figure out what happened?
Tools
Tools Required
1- Wiresahrk
Writeup
Q1
What specific technique does the attacker employ in conducting traffic analysis?
T1499
In packets number 15 and 17, a large number of requests were observed using HEADERS and RST_STREAM frames.
Q2
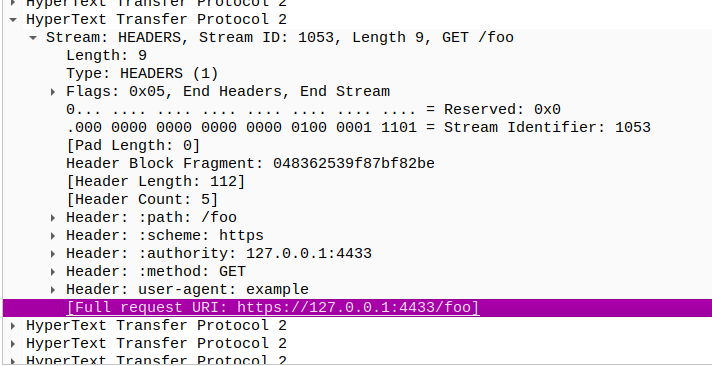
What is the full request sent?
Q3
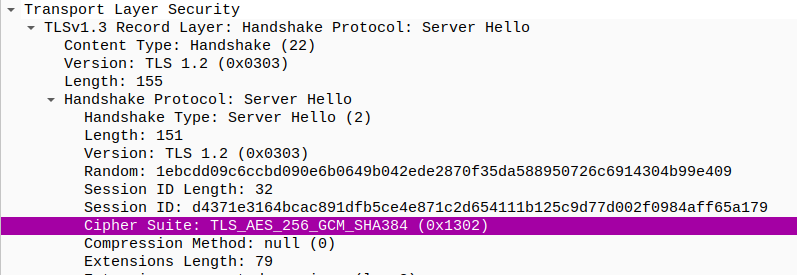
Which cipher type is utilized in the TLS packets transmitted by the server?
TLS_AES_256_GCM_SHA384
In packet number 6 or 9, we observed the use of TLSv1.3.
Q4
What is the tool name of the server hosting library being employed?
nghttpd
In packet number 16, we observed the use of the server nghttpd nghttp2/1.57.0-DEV. After conducting a search, it was found that nghttp2 is an open-source implementation of the HTTP/2 protocol in the C programming language.
Q5
Which protocols does the server support?
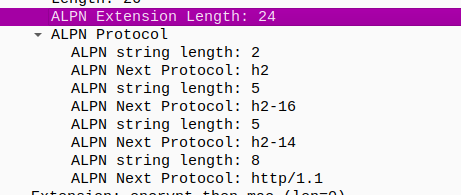
h2,h2-16,h2-14,http/1.1
By using github link we found This endpoint supports h2, h2-16, h2-14, and http/1.1 via ALPN/NPN and requires TLSv1.2 for HTTP/2 connection.
Or search by ALPN
Q6
Which specific frame in the HTTP/2 protocol is accountable for triggering this attack?
RST_STREAM
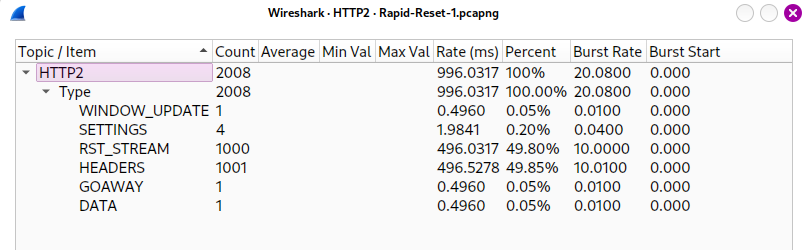
Upon analyzing all requests, a significant number of RST_STREAM frames were observed. By using HTTP/2 statistics, it was found that there were 1000 requests.
Q7
What is the status code returned by the server in its response?
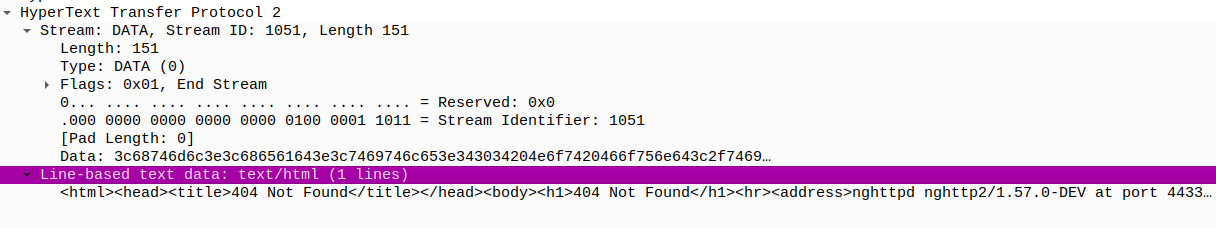
404
In packet number 16, the information field indicates a response of “404 Not Found.” Further investigation can provide additional details.
Q8
What value enables the client to generate a high request rate by churning requests?
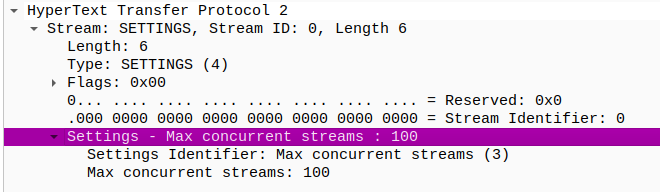
Max concurrent streams
Brief: In packet number 14, the SETTING[0] frame provides information related to this value.
Q9
How many requests were made in total?
2008
By checking the statistics or HTTP2, the total number of requests can be determined.
Statistics -> HTTP2
Q10
Which frame is responsible for closing the connection?
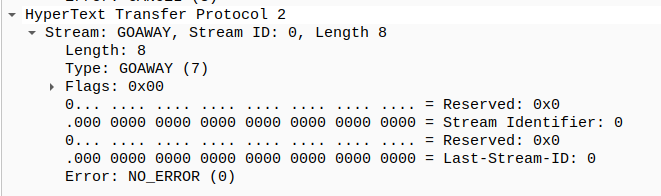
GOAWAY
I saw GOAWAY frame this frame responsible for closing the connection in packet num 17 go on the last request