
| Lab | Challenge link | difficulty | Writeup link |
|---|---|---|---|
| Lab 1 | Beginner’s Luck | Easy | Lab 1 |
| Lab 2 | A New World | Easy | Lab 2 |
| Lab 3 | The Evil’s Den | Easy - Medium | Lab 3 |
| Lab 4 | Obsession | Medium | Lab 4 |
| Lab 5 | Black Tuesday | Medium - Hard | Lab 5 |
| Lab 6 | The Reckoning | Hard | Lab 6 |
Challenge description
My sister's computer crashed. We were very fortunate to recover this memory dump.
Your job is get all her important files from the system. From what we remember,
we suddenly saw a black window pop up with some thing being executed. When the
crash happened, she was trying to draw something. Thats all we remember from
the time of crash.
- Note: This challenge is composed of 3 flags.
Writeup
Stage 1
our first Step will be checking the image info to know which profile will be used in the analysis
.\volatility.exe -f .\MemoryDump_Lab1.raw imageinfo
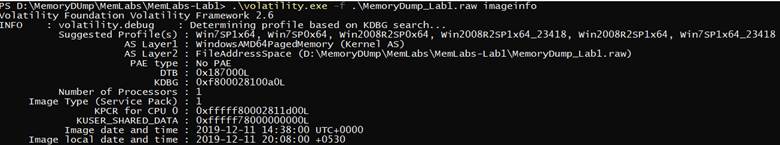
As we see it “Win7SP1x64”
So let’s start check the process and see if there are anything suspicious
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 pslist
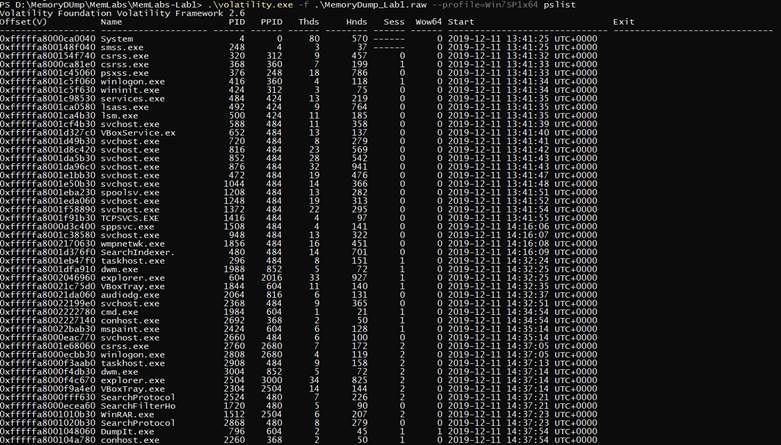
So we found cmd.exe that was running so we scanned it
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 cmdscan
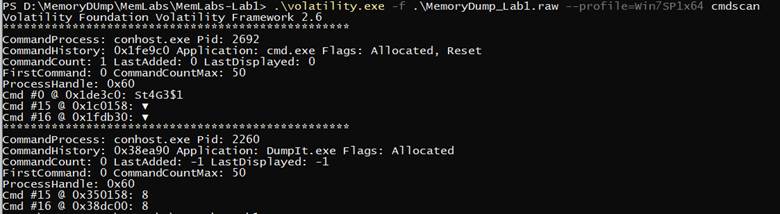
we found that he typed something interesting in cmd called (“St4G3$1”) So lets check the consoles
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 consoles
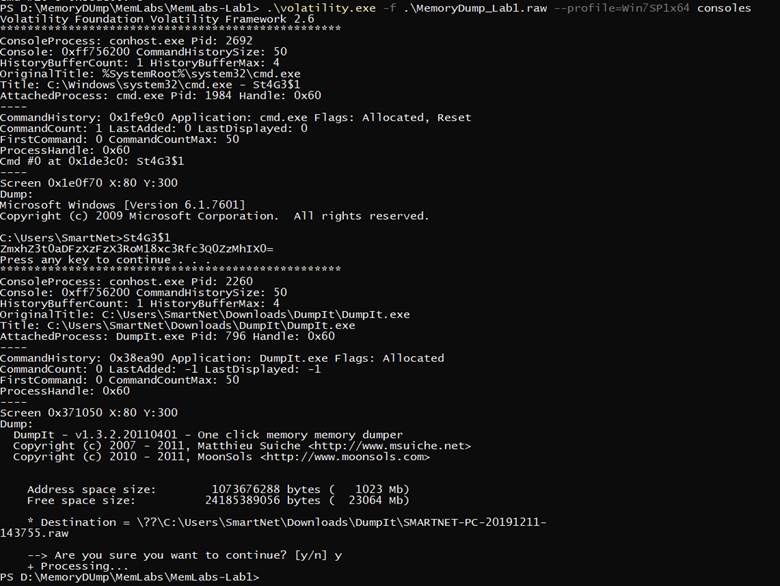
there was base 64 Text after decoding we got the first flag
flag{th1s_1s_th3_1st_st4g3!!}
Stage 2
for the next flag We checked process again and found that there is process called (“mspaint.exe”) so let’s dump it
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 memdump -p 2424 -D output

we changed the extension of the dump from .dmp to .data to be raw image data so we can open it using GIMP
So it’s a not making any sense so we tried to change the heights and widths

We got this so let’s reverse it and see what it says

and we got the 2nd flag flag{G00d_BoY_good_girL}
Stage 3
while we were checking the processes we noticed that winrar was running
so we did a file scan
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 filescan
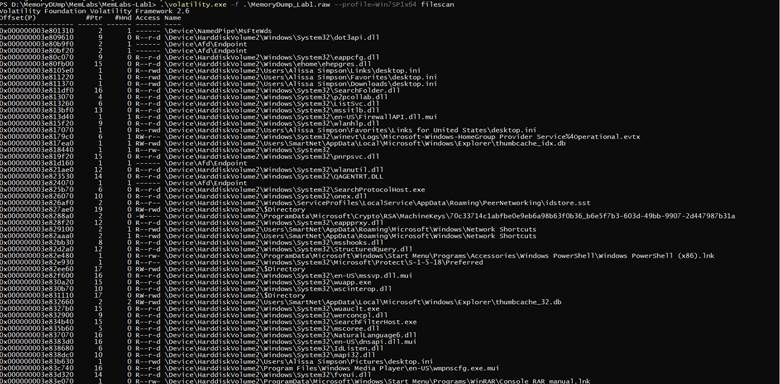
Okay that’s a lot of files so Winrar uses ( .zip , .rar ) so let’s grep them
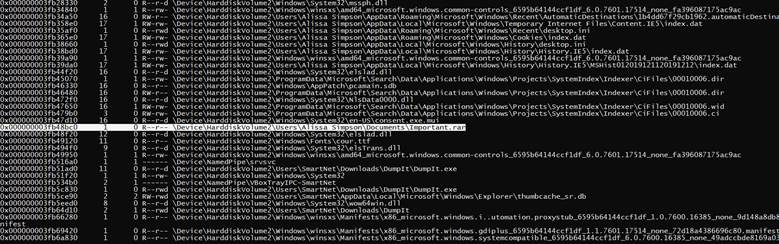
there was a file called important so we extract it
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003fa3ebc0 -D output
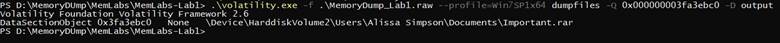
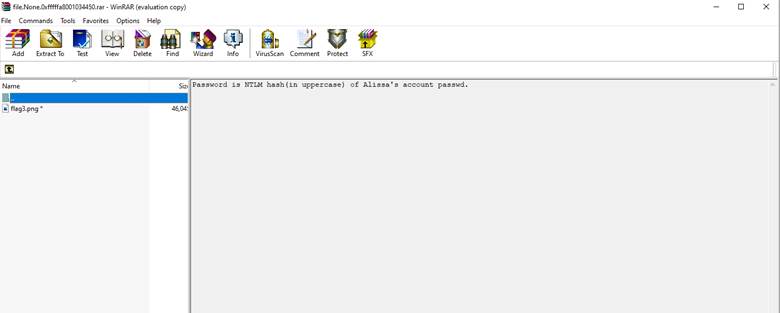
we got the rar but it’s password protected to get the password we have to get the NTLM hash by using hashdump
.\volatility.exe -f .\MemoryDump_Lab1.raw --profile=Win7SP1x64 hashdump
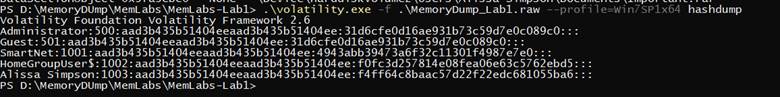
we got the password
F4FF64C8BAAC57D22F22EDC681055BA6
the 3rd flag is:
flag{w3ll_3rd_stage_was_easy}