
| Lab | Challenge link | difficulty | Writeup link |
|---|---|---|---|
| Lab 1 | Beginner’s Luck | Easy | Lab 1 |
| Lab 2 | A New World | Easy | Lab 2 |
| Lab 3 | The Evil’s Den | Easy - Medium | Lab 3 |
| Lab 4 | Obsession | Medium | Lab 4 |
| Lab 5 | Black Tuesday | Medium - Hard | Lab 5 |
| Lab 6 | The Reckoning | Hard | Lab 6 |
Challenge description
A malicious script encrypted a very secret piece of information I had on my system.
Can you recover the information for me please?
This challenge is composed of only 1 flag. The flag split into 2 parts.
You’ll need the first half of the flag to get the second.
You will need this additional tool to solve the challenge
sudo apt install steghide
The flag format for this lab is: inctf{s0me_l33t_Str1ng}
Writeup
Part 1
as always we will use image info to get the profile
./volatility.exe -f MemoryDump_Lab3.raw imageinfo
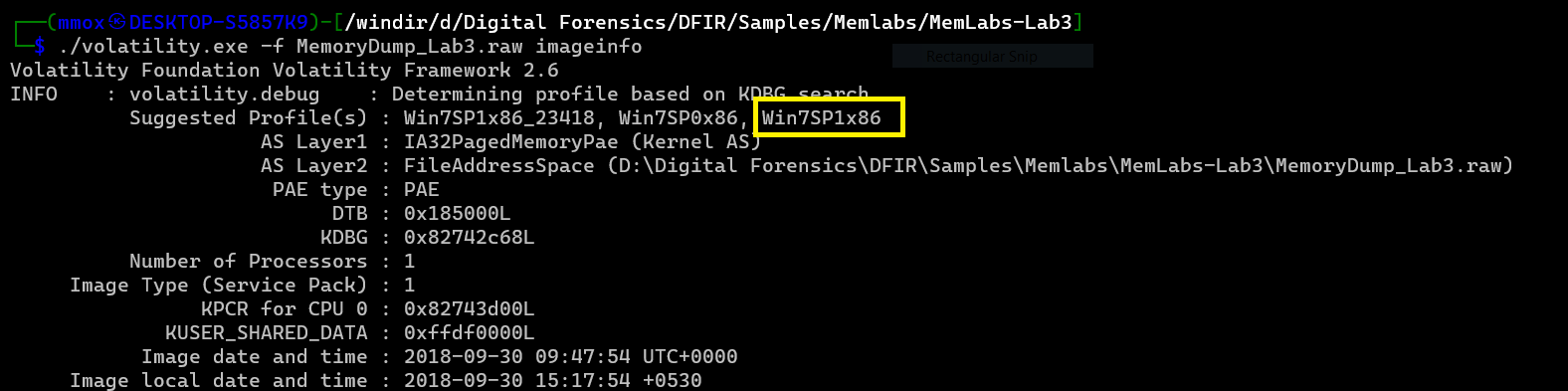
so this time it’s “Win7SP1x86”
by doing cmdline
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 cmdline
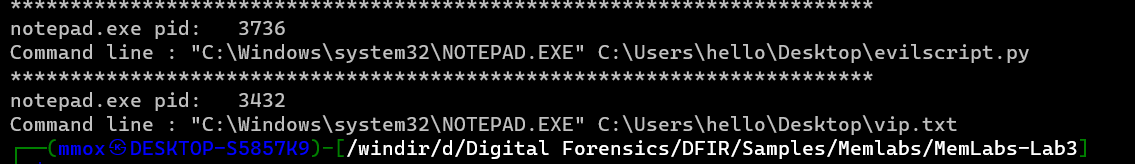
we found 2 files “evelscript.py” and “vip.txt” so we will do file scan and grep the 2 files for extraction
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 filescan |grep "evilscript.py"
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 filescan |grep "vip.txt"
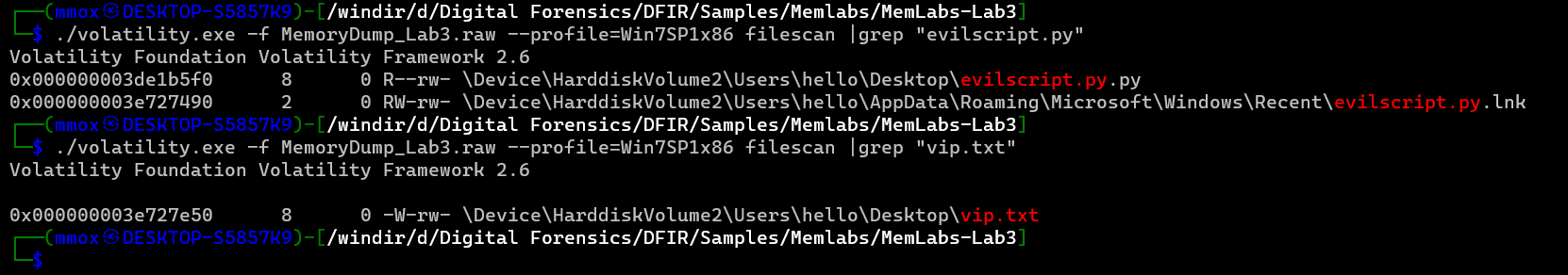
after dumping them using dumpfiles with the offset
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 dumpfiles -Q 0x000000003e727e50 -D .
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 dumpfiles -Q 0x000000003de1b5f0 -D .
the “vip” text was :
am1gd2V4M20wXGs3b2U=
the script was easy to analys:
import sys
import string
def xor(s):
a = ''.join(chr(ord(i)^3) for i in s)
return a
def encoder(x):
return x.encode("base64")
if __name__ == "__main__":
f = open("C:\\Users\\hello\\Desktop\\vip.txt", "w")
arr = sys.argv[1]
arr = encoder(xor(arr))
f.write(arr)
f.close()
- take input
- xor it with key 3
- encoded to base64
- write it in the vip file
so we will do the oppsite we will take the text from the vip file and by using CyberChef we will get the first half
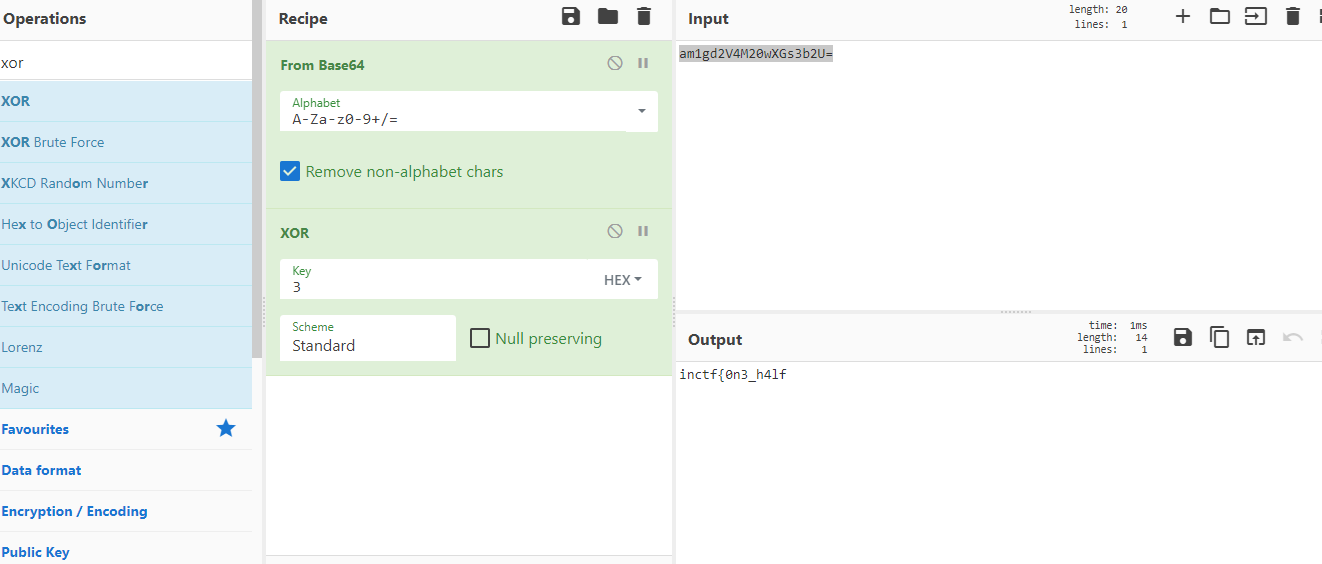
now we have the first part
inctf{0n3_h4lf
Part 2
he provided us with a tool to use with is “steghide” as we know it’s stegnography tool so let’s serch again for jpg ,jpeg and png
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 filescan |grep ".jpg"
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 filescan |grep ".jpeg"
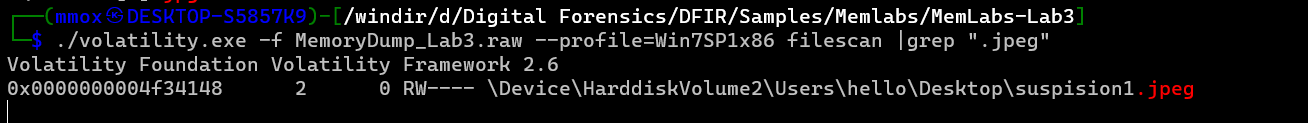
by getting the jpeg files there was only 1 file called “suspision1.jpeg” let’s dump it and as I use windows I had to rename it
./volatility.exe -f MemoryDump_Lab3.raw --profile=Win7SP1x86 dumpfiles -Q 0x0000000004f34148 -D .

by using steghide and assuming the first half is the passphrase we goth the second half easly
steghide extract -sf suspision1.jpeg -p inctf{0n3_h4lf
cat secret\ text
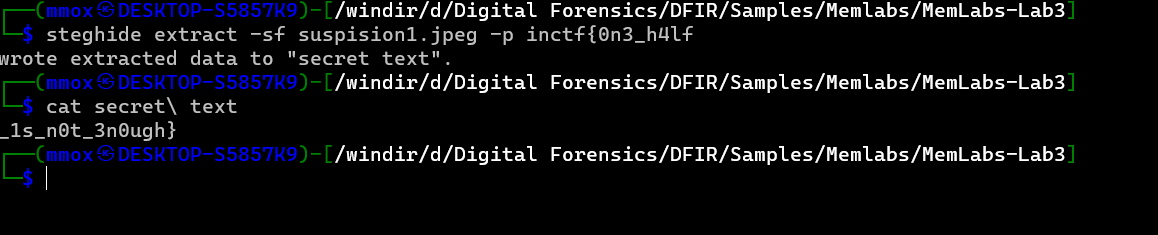
so the flag was
inctf{0n3_h4lf_1s_n0t_3n0ugh}