
| Lab | Challenge link | difficulty | Writeup link |
|---|---|---|---|
| Lab 1 | Beginner’s Luck | Easy | Lab 1 |
| Lab 2 | A New World | Easy | Lab 2 |
| Lab 3 | The Evil’s Den | Easy - Medium | Lab 3 |
| Lab 4 | Obsession | Medium | Lab 4 |
| Lab 5 | Black Tuesday | Medium - Hard | Lab 5 |
| Lab 6 | The Reckoning | Hard | Lab 6 |
Challenge description
We received this memory dump from the Intelligence Bureau Department. They say this evidence
might hold some secrets of the underworld gangster David Benjamin. This memory dump was taken
from one of his workers whom the FBI busted earlier this week. Your job is to go through the memory
dump and see if you can figure something out.FBI also says that David communicated with his
workers via the internet so that might be a good place to start.
- Note: This challenge is composed of 1 flag split into 2 parts.
- The flag format for this lab is: inctf{s0me_l33t_Str1ng}
Writeup
Part 1
it was Win7SP1x64 so i did pslist
./volatility.exe -f MemoryDump_Lab6.raw --profile=Win7SP1x64 pslist
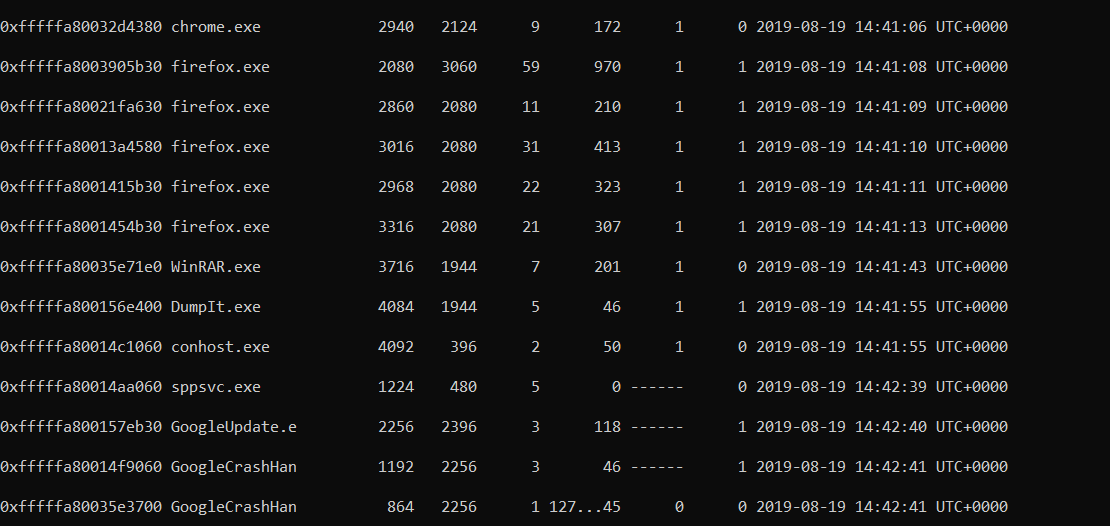
from the process list chrome.exe, firefox.exe and WinRAR.exe as active running processes.
so i used Volatilty plugins you can git it from github
volatility --plugins=/home/mmox/vplug -f MemoryDump_Lab6.raw --profile Win7SP1x64 chromehistory
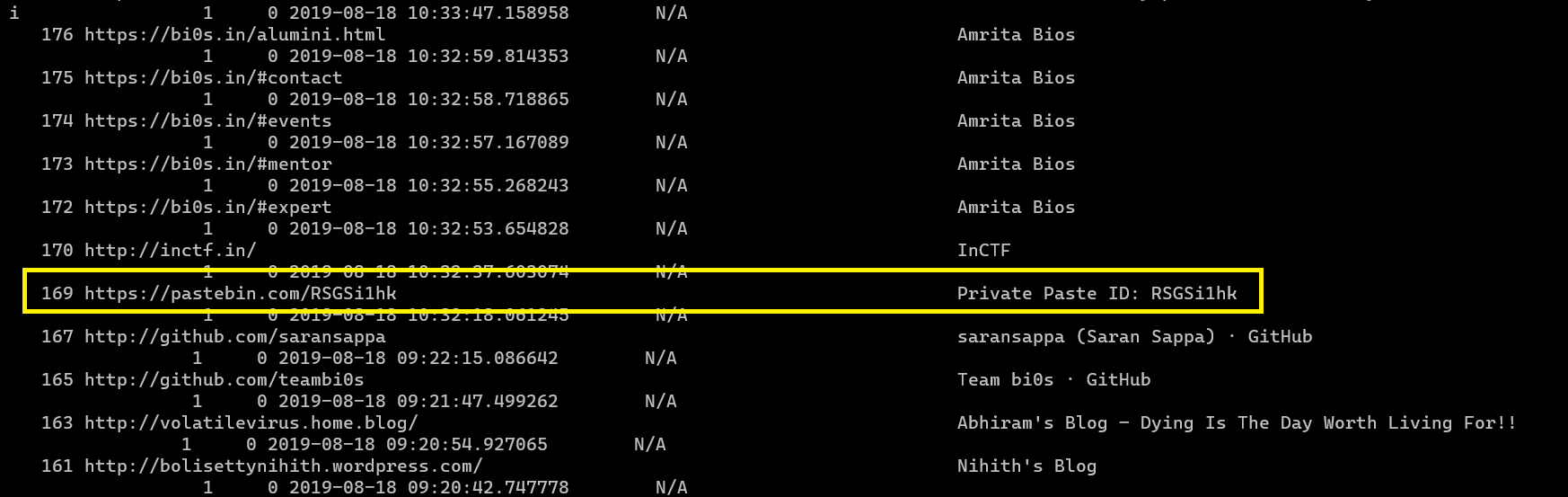
https://pastebin.com/RSGSi1hk
when i opend the link there was a google doc link
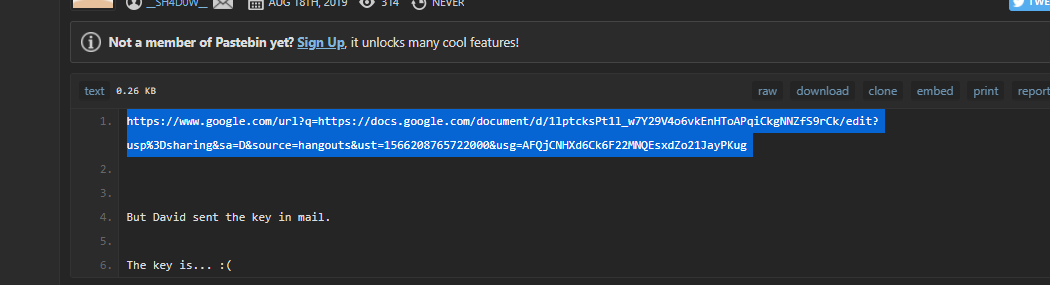
https://www.google.com/url?q=https://docs.google.com/document/d/1lptcksPt1l_w7Y29V4o6vkEnHToAPqiCkgNNZfS9rCk/edit?usp%3Dsharing&sa=D&source=hangouts&ust=1566208765722000&usg=AFQjCNHXd6Ck6F22MNQEsxdZo21JayPKug
while going throw the doc i found a mega link
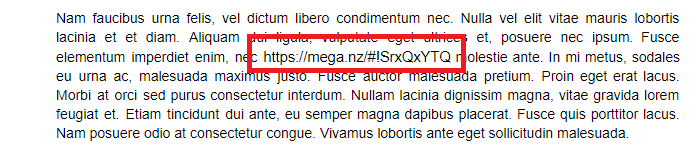
https://mega.nz/#!SrxQxYTQ
it was missing the decryption key in the pastebin link there was this text so But David sent the key in mail.
The key is... :(
so i will try something stupid
strings MemoryDump_Lab6.raw |grep -i "The key is"
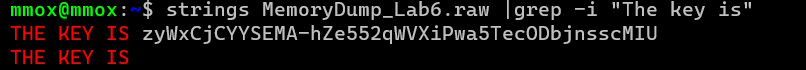
I was not expected that actually but work smarter not harder by using the key
zyWxCjCYYSEMA-hZe552qWVXiPwa5TecODbjnsscMIU
i was able to download the flag_.png file but it wasn’t working so i checked the hex header
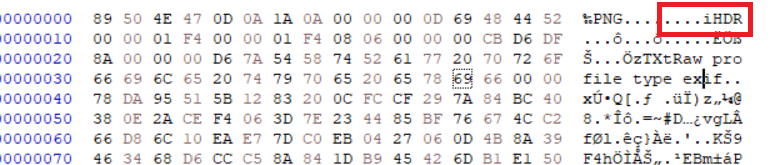
really simple by replacing the “i” of “iHDR” with a captal “I” it worked
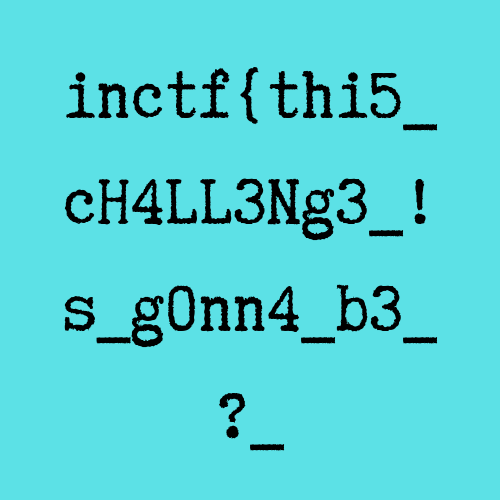
and that was the first part :
infctf{thi5_cH4LL3Ng3_!s_g0nn4_b3_?_
Part 2
it was a really long way to get the first half now let’s get the second one
there was a winrar process running so we will check the files and grep RARs
./volatility.exe -f MemoryDump_Lab6.raw --profile Win7SP1x64 filescan |grep ".rar"
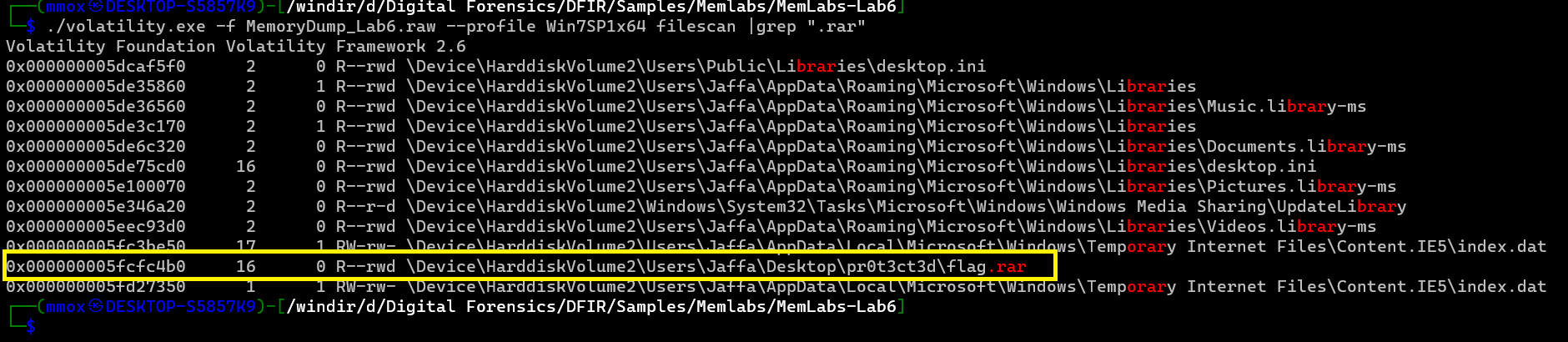
there was a rar calld flag.rar so let’s dump it
./volatility.exe -f MemoryDump_Lab6.raw --profile Win7SP1x64 dumpfiles -Q 0x000000005fcfc4b0 -D .
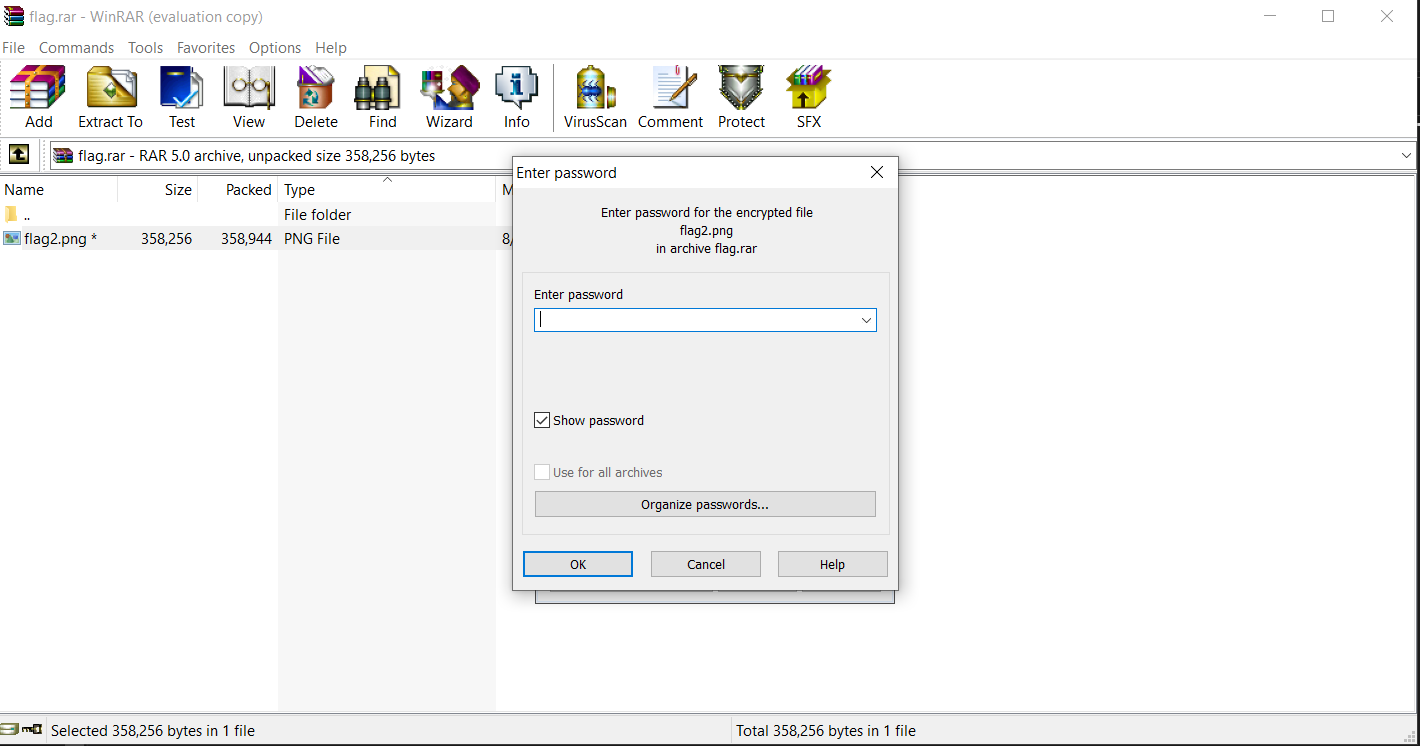
ops it’s password protected so i tried a lot to get the password using “cmdline”,“cmdscan”,“greping text files”, “greping images”,“consoles "
but finally i found it in envars
./volatility.exe -f MemoryDump_Lab6.raw --profile Win7SP1x64 envars
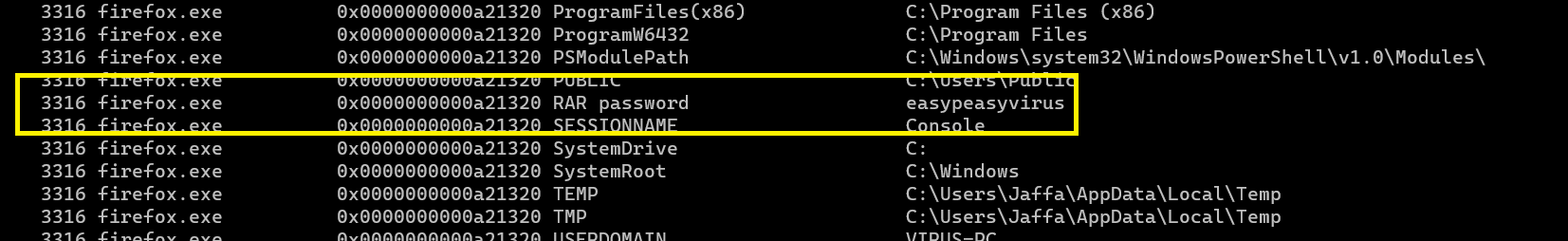
easypeasyvirus
by using it i extracted flag2.png from the rar file

and that’s it the second half
aN_Am4zINg_!_i_gU3Ss???_}
it was the hardest one but i got the flag :
infctf{thi5_cH4LL3Ng3_!s_g0nn4_b3_?_aN_Am4zINg_!_i_gU3Ss???_}